
Many Multi-factor Authentication (MFA) tools have a problem: they aren’t very good at measuring the risk of a login attempt. They’ll allow high-risk logins to go through without prompting the user for another factor, such as a one-time password. And they’ll prompt users for MFA even when they are performing a low-risk login attempt. The root cause is that these MFA tools are using simplistic IP allow listing to incorrectly score risk levels.
Smart Risk Scores
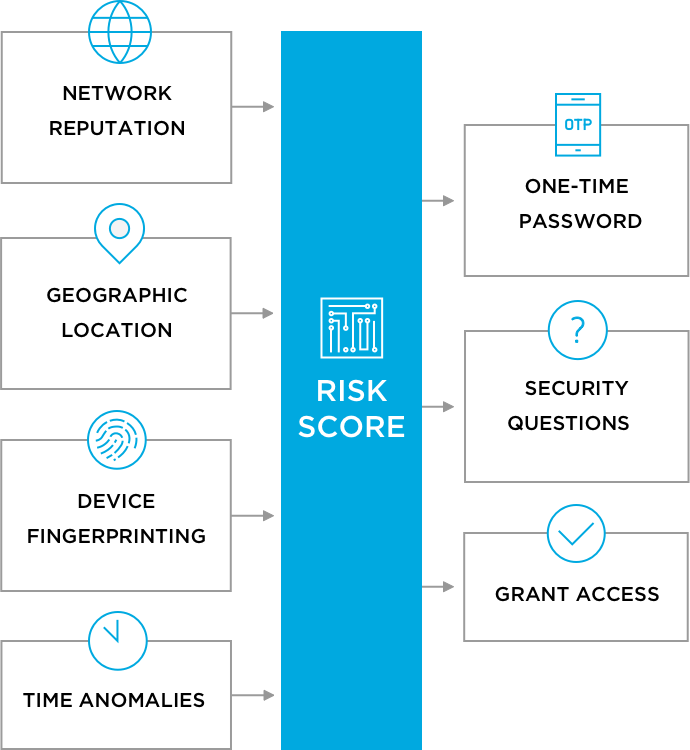
What’s needed is a smarter way to score risk, so we know when MFA should be required, and when it shouldn’t be. That’s what we’ve done with OneLogin Adaptive Authentication, which we just released. Built for security teams who need to reduce the risk of account takeovers, Adaptive Authentication intelligently scores the risk of each login attempt, and challenges users making high-risk logins to use an additional authentication factor.
OneLogin Adaptive Authentication uses a broad set of inputs related to networks, geography, devices, and time to build profiles of typical usage patterns. The greater the deviation from typical usage, the higher the risk score. Risk scores will also be increased by network traffic coming in from an IP address with low trust (such as Tor exit relay), a deny listed country or city, or from two locations that are far apart.
Easy Integration
Using OneLogin Adaptive Authentication doesn’t require you to change your existing multi-factor authentication provider. Users that attempt logins with high risk scores can be prompted to submit a second factor from Duo, Google Authenticator, Symantec VIP Access, Yubico Yubikey, and RSA SecurID. They can also be prompted using OneLogin OTP (one-time password) mobile app, SMS, or security questions.
Usability Drives Adoption
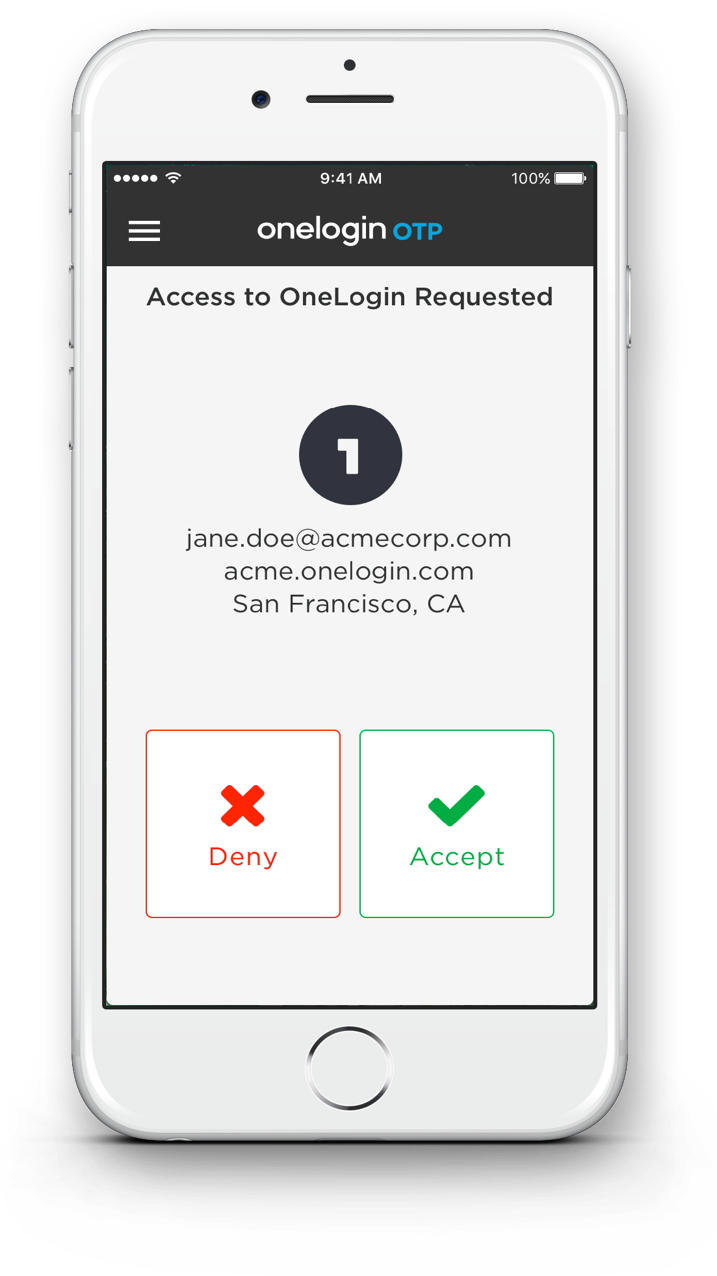
Speaking of OneLogin OTP, that brings us to a second announcement: OneLogin OTP has been upgraded to streamline the user experience. When a user is prompted for a second factor, they see a push notification on their phone or Apple Watch, and can choose to Accept or Deny a login attempt. By reducing friction, you increase the usage of MFA among your end users, which in turn improves your security posture.
Better Together
OneLogin Adaptive Authentication and Push MFA make a great combination. They make it easy to implement multi-factor authentication for the OneLogin Application Portal, your SAML applications, VPN, and WiFi. (VPN and WiFi authentication use our VLDAP and Cloud RADIUS services.)
Adaptive Authentication lets you mitigate security risks that IP allow listing fails to detect, and avoids interrupting users with MFA authorization requests for low-risk login attempts — and when users receive an MFA request, they have a simple way to respond.
Pricing & Availability
Push MFA is in OneLogin OTP 2.2 for iOS, a free upgrade now on the Apple App Store, and will soon be available on Android. If you’re already using OneLogin OTP, it’s an automatic upgrade like any other iOS app.
OneLogin Adaptive Authentication is available now; pricing is on our website. Please contact us to learn more.

