You probably know that authentication is central to cybersecurity, and that the evolution to multi-factor authentication (MFA) has helped better secure access. But cybercriminals are constantly evolving their tactics as well, including adding artificial intelligence (AI) to their toolkit. Which is why identity and access management systems are rapidly implementing very sophisticated AI to further strengthen MFA.
Authentication is an early and critical line of defense for business data. But, traditional authentication based on passwords remains a weak point. That’s because users are notorious for bad password practices:
- Reusing passwords
- Using predictable ones
- Storing password information on sticky notes or in unencrypted spreadsheets
As a result, more and more companies are adding multi-factor authentication (MFA), even for their customer experiences, requiring customers making a product purchase or conducting a bank transaction from their phone to further authenticate. By adding additional factors beyond the password—or, even better, in place of the password—businesses can help thwart password spray and social engineering attacks and stop hackers using stolen credentials from ever entering the account. Additional factors might include answering a security question, using a one-time password, or responding to a push notification on the phone.
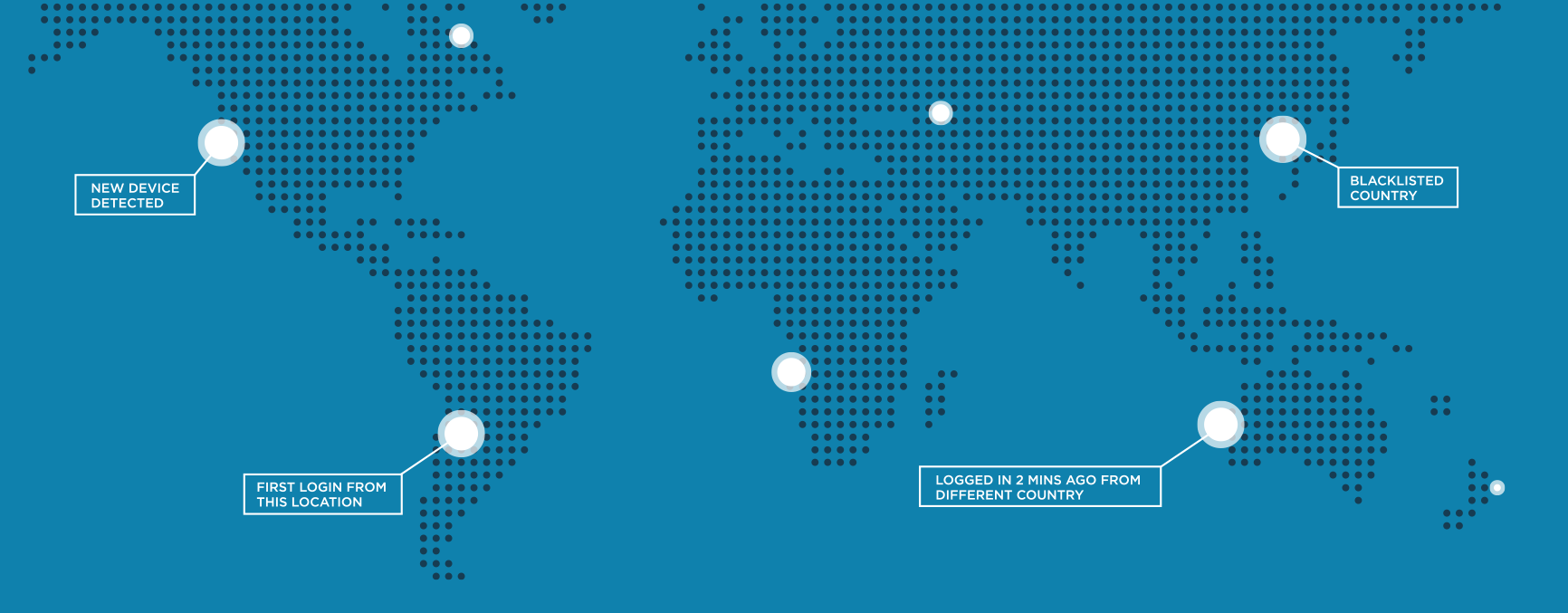
Hackers are clever, though, and even with MFA people’s accounts can be compromised. Devices, like phones or USBs, can be stolen. One-time passwords transmitted via SMS can be intercepted. And biometrics, such as fingerprints and even facial recognition, can be hacked or faked. As artificial intelligence gains traction, it becomes even easier to fake even biometrics, making fake fingerprints and facial images with enough matching points to pass a scan. But MFA can be improved by adding a critical piece of information: context. Context is the information about the user’s login, like where the user is when attempting to log in or the device being used. Such context can provide critical clues that an attack is happening.
Risk-based authentication
To add context, the identity and access management (IAM) industry has responded with risk-based authentication. Standard MFA captures information about what the user knows, like a password, what the user has, like his or her phone, and even who the user is via biometrics such as fingerprints. Risk-based authentication allows for additional factors that help determine if the user really is who they say they are. This is done by comparing their past login behavior to the current authentication attempt, providing context information that is missing in standard MFA.
For example, if a user usually logs in on a particular laptop from the main office location during the week but suddenly tries to log in from a phone at Starbucks, it may be a sign of a stolen laptop or compromised account.
Or, if the user typically logs in from home via one IP address and suddenly is logging in from another IP address—perhaps one on a list of suspicious IPs—you would want to challenge the login attempt and ask for an additional authenticating factor like a one time password or face scan from a token device. Assessing authentication data like this in real-time requires intensive and sophisticated processing. That’s where artificial intelligence comes in.
![AI authentication]](https://s39948.p1254.sites.pressdns.com/wp-content/uploads/2022/01/ai-authentication-topics-image.jpg)
Enter AI
To implement risk-based authentication, companies like OneLogin, use AI-backed technologies. The AI assesses and weighs individual factors about the login attempt to come up with a risk score for the scenario. For example, a user connecting from certain IP addresses or attempting to log in during the middle of the night might indicate a threat.
AI can also use neural networks as part of machine learning systems. These neural networks mimic the human brain and “learn” by being fed datasets that include the correct result. For example, data about logging in via different IPs and the results indicating which of those logins were cyberattacks. It’s like a kid given an algebra problem and the answer, who must figure out what the formula is to solve this type of algebra problem. The AI develops better and better algorithms to determine which factors indicate an attack by trying different techniques to solve the problem and checking its answer against the answer in the dataset. Eventually, it finds a set of algorithms that enable it to accurately predict threats most of the time.
How does AI help provide better, more secure authentication?
Risk engines, like OneLogin’s Vigilance AI™, monitor a number of factors in a user’s logins over time and build a profile for each user to understand login patterns. When a user varies from that profile on a given authentication attempt, the AI system assesses the variable factors and determines a risk score for the current login attempt. Some of the factors typically accounted for include:
- Network reputation
- User’s geographic location
- The device fingerprint (such as the manufacturer, model, or browser)
- Time of login
The final output of the analysis is a risk score that can dictate actions. For example, based on the risk score, OneLogin’s SmartFactor Authentication™ adjusts authentication requirements. If the risk score is high, OneLogin might ask for another authentication factor like a fingerprint scan. Or, depending on your settings, the platform might deny the login entirely.
While the key benefit of AI-powered risk-based authentication is security, it can also streamline the authentication process. In standard MFA, users are prompted for additional factors at every login attempt. Enter your username and password, then answer a security question. Or enter your username and password, then respond to a push notification on your phone. With AI-powered authentication, users at low risk might not be asked for any additional factors, making login faster.
What’s the future of AI in authentication?
Risk-based authentication will continue to improve and get smarter. Eventually, risk-based authentication will likely move from supervised learning, where the dataset includes the outcomes, to unsupervised learning where the AI finds new patterns that humans may not have discovered and makes predictions of potential factors to assess. Being able to cross reference multiple machine learning algorithms and use pattern recognition and time-series based predictive algorithms will improve the accuracy and scope of AI-based authentication offerings going forward, for web application logins, but also for other aspects of cybersecurity such as network intrusion and botnet detection.
At the same time, developers will be looking for ways to give IT departments more control over the AI system, such as the ability to understand exactly why the AI made a given decision, adjust the number of factors being considered, and tailor the system to their organization’s unique environment. One area that companies, like OneLogin, are already investigating is the ability to consume third-party data. OneLogin’s SmartFactor Authentication includes a compromised credential check that uses third-party data on stolen or exposed credentials. Although not strictly AI, various cross-industry initiatives are underway to enable better data-sharing so that the information one organization has on a potential threat can be made available to other organizations in real-time, improving MFA.
You can also expect to see AI-powered authentication systems expand to encompass continuous authentication. Instead of real-time threat assessment just at login, AI systems will detect and respond to threats throughout a user’s session. If the user suddenly moves to a new location and device, or attempts to access financial information that isn’t relevant to their work, they’ll be prompted to verify their identity.
And even further out, access management will likely move from the application level to the data level. Experts are already talking about attaching metadata to individual pieces of data, to indicate who should have what type of access to that discrete piece of information. For example, the field in a database containing employee salaries would have metadata indicating that only users within the company who hold certain roles can view that information. Whenever that salary information is exported or shared, the restrictions on access would be shared with it. AI-powered authentication would then enforce these data-level access restrictions wherever the data is used.
As identity and access management requirements evolve, so will AI as a tool in IAM. Because, the fact is, AI is necessary to manage the complexity of analysis at the scale and speed that will be needed in the changing threat landscape and the evolving identity and access management environment.
For more information, explore Securing the Future of Identity with AI.