
Situation:
As I was reading some amazing stats from Microsoft like the recent Azure Active Directory (AAD) milestone of having just completed their 1 trillionth authentication, I had to acknowledge this feat out of sheer respect for the organization’s achievement.
Yet, at the same time I read about Microsoft’s new Azure AD Connect which was previewed this week (beta started in August), and is anticipated to be GA in May 2015. Azure AD Connect is intended to be Microsoft’s single tool for simplifying the AD premises-to-cloud connection process, including Office 365.
Azure AD Connect reflects Microsoft’s decision to move all their directory synchronization engines, including password synch, into Azure AD Connect. Microsoft has stated that Azure AD Connect is going to replace all other connecter tools in the Microsoft bag of tricks, including: Azure AD Sync (which in September was presented as the “one sync to rule them all”), and Office 365 DirSync (first introduced in 2008),
Of course most people I’ve spoken with say “what is Azure AD Connect?”. Perhaps more importantly, IT Admins view this with mixed emotions- either it’s 1) Yeah, they’re finally solving my problem and providing just one tool, or 2) Darn, I was just getting familiar with X, and now have to plan on implementing an entirely new tool.
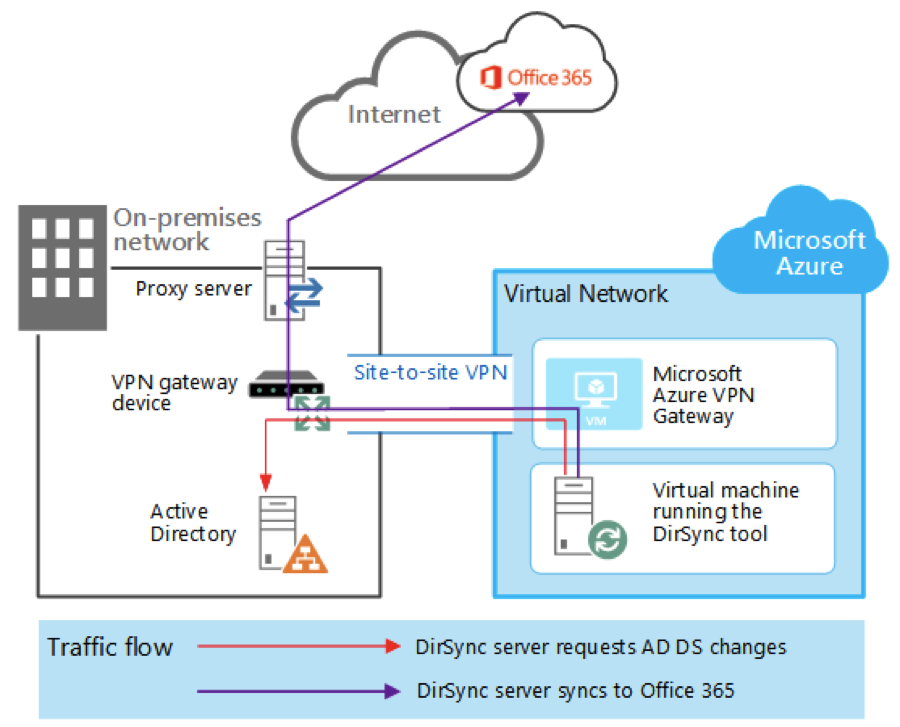 Figure: Previous approaches such as DirSync to align AD to Office 365
Figure: Previous approaches such as DirSync to align AD to Office 365
Challenge:
With the introduction of Office 365 in 2011 the question arose, “how best to authenticate my users to Office 365?” Historically, synchronizing AD user credentials to Microsoft’s cloud-based apps like Office 365 has been received with mixed response. When Windows XP and Office 2003 entered End of Support earlier this year, one of the migration recommendations was to adopt Windows 8.1 and Office 365. However, the complexity of extending Active Directory to the Office 365 infrastructure, and providing utilities supporting single sign-on functionality for the hundreds if not thousands of other non-Microsoft cloud applications being rolled out posed a problem. This helped open the door for providers like OneLogin who offer powerful AD integration features, strong authentication, and an expansive catalog of cloud application connectors.
If Azure AD Connect is a path forward, some questions I would ask are: What additional Microsoft infrastructure is going to be required for AAD Connect to support my AD to Office 365 integration, How flexible is ADD Connect to not only bridge my AD to O365, but also AD to potentially hundreds of other cloud apps I have not tied to Azure.
Inevitably the question arises with Microsoft- does the breadth of functionality meet my needs, and when is good enough actually good enough? What are the total costs of implementing the options at my disposal? Would proven cloud offerings such as OneLogin, that have robust Active Directory integrations and Office 365 connector support, be a better architecture and business decision going forward?
Action:
Microsoft shops are in a wait and see mode- i.e. cautiously optimistic. Perhaps the best thing you can do is to evaluate the Azure AD Connect preview alongside OneLogin, and assess your experience.
The fact that the minute I started writing about the advantages of OneLogin Active Directory Integration versus Microsoft Azure Directory Synchronization (DirSync) for Office 365, the Microsoft product strategy shifted to AAD Connect. The reality given this flux is that we all have to move forward and make the best strategic decisions possible at the time . Once you’ve had a chance to digest the revised Microsoft strategy for solving the on-prem Windows Server Active Directory to Azure Active Directory integration challenge, I suggest outlining a plan that takes into consideration Microsoft’s latest roadmap. You should define a shortlist of vendors that can address your problem, and OneLogin should be on this shortlist.
Result:
Azure and other Microsoft cloud solution providers are once again being asked to shuffle their tools, move data, and try something new. I suspect Microsoft will continue to evolve their strategy as the organization changes, which could very well impact the Active Directory team. Perhaps it is time to evaluate options, explore 3rd party solutions focused on solving this problem, i.e. authenticating your Windows users to the thousands of cloud applications available that aren’t necessarily based on Azure. It’s time to look outside Microsoft to extend your identity infrastructure to the cloud.
I would recommend looking at best of breed cloud identity-as-a-service (IDaaS) providers like OneLogin to solve these problems. OneLogin’s core business is built on cloud identity management, based on a platform built for IDaaS. OneLogin has a proven architecture and solution which integrates easily with Active Directory, provides better security across your broader cloud app portfolio, improves IT and user productivity, reduces capital and operational costs, and delivers comprehensive visibility into identity and access for compliance.

