
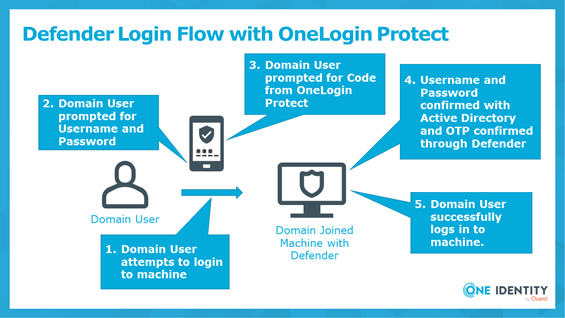
With OneLogin’s recent acquisition by One Identity we have been eager to see how we can start integrating our full portfolio of products together to deliver our Unified Identity Security Platform. This blog is the first in a series of blogs highlighting these integrations as they evolve along the way. One of the solutions our OneLogin team was most excited to see in the One Identity portfolio was One Identity Defender. For those who are not familiar with Defender, it enhances your security by requiring users to provide an additional authentication factor when they are trying to access network resources. This is exactly what many of OneLogin’s customers had been looking for: a Device Level Multi Factor Authentication (MFA) solution.
As a result, one of the first integrations we explored was how OneLogin and Defender could work together out of the box. We identified two options:
- Using OneLogin Protect as a Defender Authentication Factor
- Using OneLogin’s RADIUS Endpoint as an Authentication endpoint for Defender
Our intent in this first blog is to give you an overview of what these foundational integrations look like and how you can easily configure them. Keep in mind, these are simple, out-of-the-box integrations. Our engineering teams are working hard in the back end to provide even more robust functionality in the future, so stay tuned.
But first, what can we do today?
Use OneLogin Protect as a Defender Authentication Factor
This configuration simply entails registering OneLogin Protect as a Defender authentication factor using the Defender web portal and, for now, choosing the Google Authenticator option, but using OneLogin Protect instead of Google Authenticator. This is a simple option that would be easy for anyone that has One Identity Defender already configured in their environment.
The key steps that need to be completed for this to work are:
- A working deployment of the One Identity Defender product.
- Domain Users register OneLogin Protect as one of their Defender authentication
We will not go into all the steps needed to install and configure Defender. You can find them in our support portal. The extra piece we are simply adding is registering OneLogin Protect as an authentication factor. This can easily be accomplished by your domain users.
- Log in to the Defender Management Portal
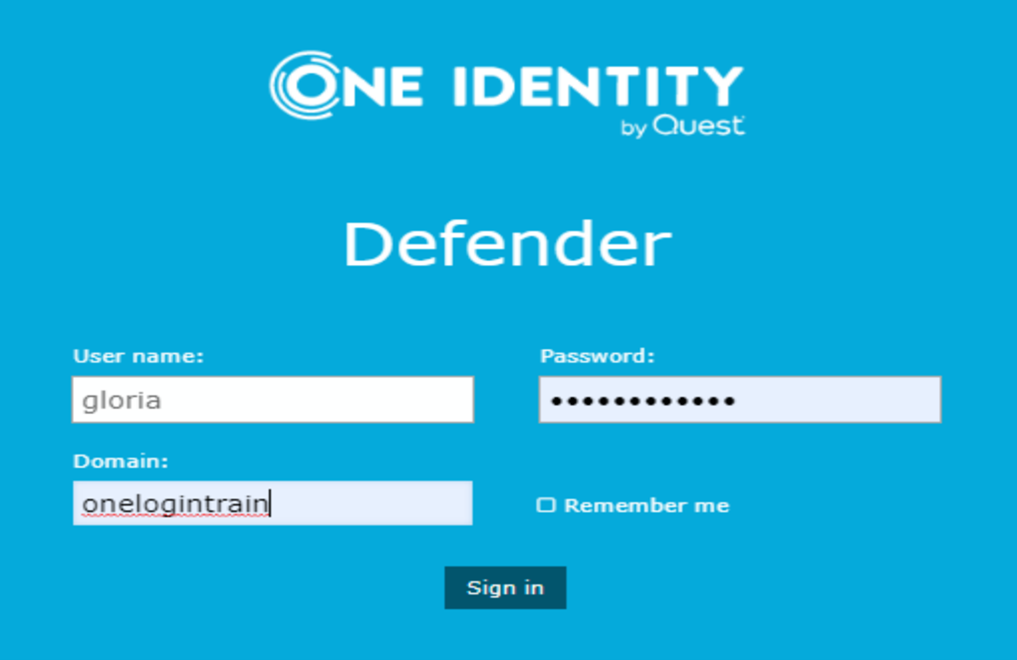
- Select Request a software token

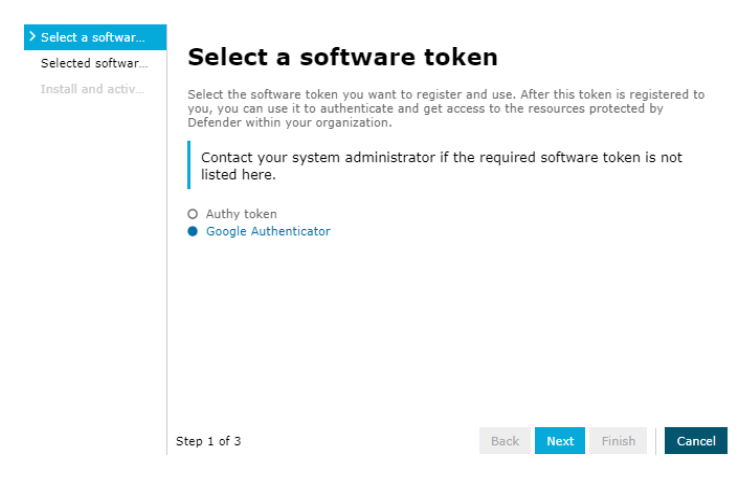
- Select Google Authenticator and click Next
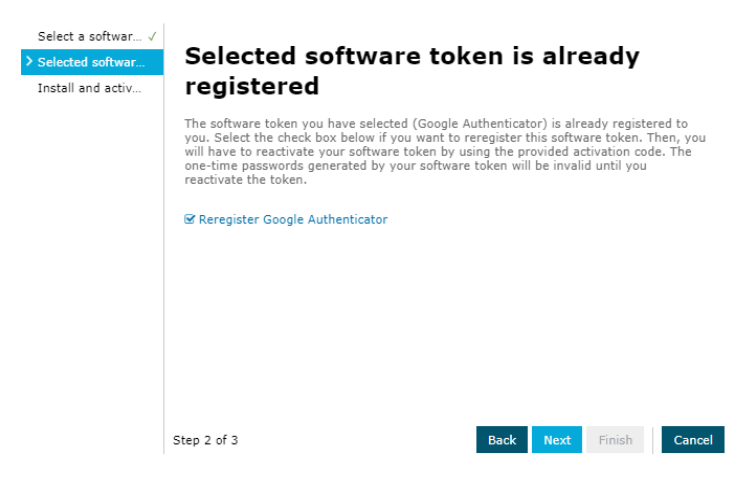
- Check Reregister Google Authenticator and click Next
- Download OneLogin Protect to your mobile device and scan the QR code.
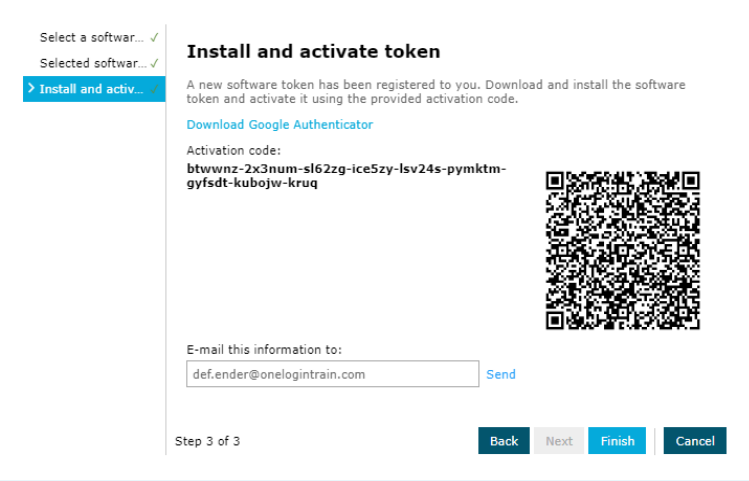
- Click Finish
It’s as simple as that.
Using OneLogin’s RADIUS Endpoint as an Authentication Endpoint for Defender
This configuration allows OneLogin customers that are synchronizing their users with the OneLogin Active Directory Connector to enable device level MFA that allows their users to log in to their work machines with their AD/OneLogin credentials and utilize any of the One-Time Password (OTP) based authentication factors they have registered through their OneLogin profile.
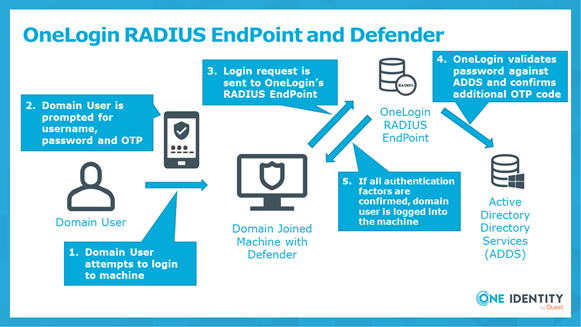
This configuration would also require Defender to be installed and configured into the Active Directory environment.
The trick is configuring the OneLogin RADIUS endpoint as an Access Node for Defender and, of course, configuring a OneLogin RADIUS endpoint that will accept requests from the server that the Defender Security Server has been installed on.
An example of the Access Node needed on the Defender end would look like this:
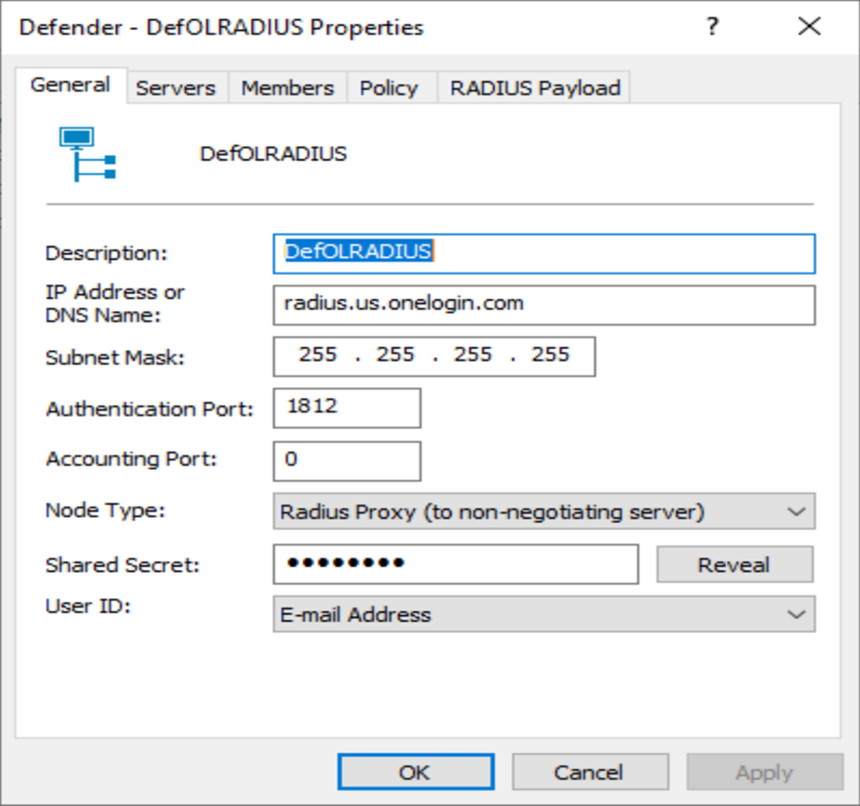
You would want to create two of these Access Nodes, one for “radius.us.onelogin.com” and one for “radius2.us.onelogin.com”. The Shared Secret would need to match the Secret you define on the OneLogin RADIUS endpoint.
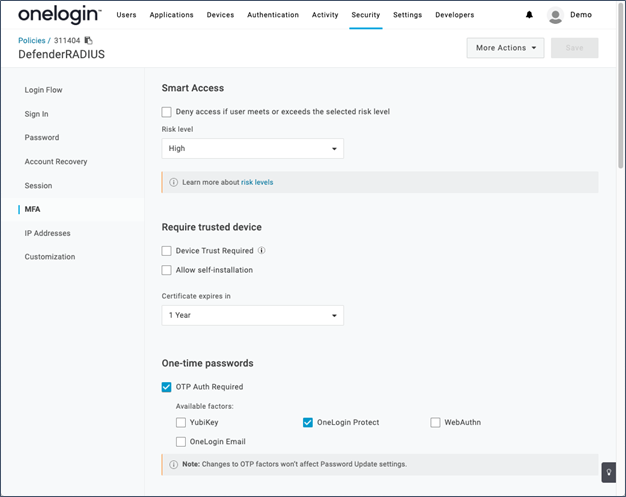
You can find instructions on how to configure RADIUS within OneLogin here. For this configuration to work your configuration will end up looking something like this:
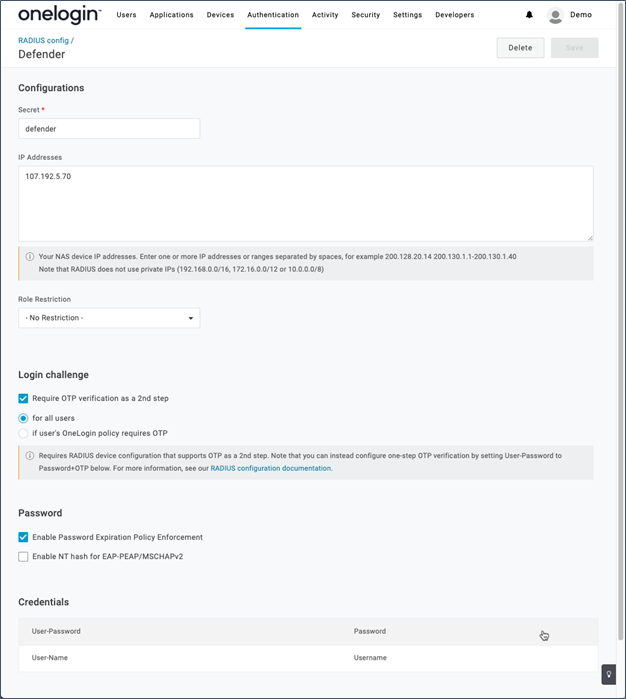
Make sure:
- The Secret here matches the Shared Secret set on the Defender Access Node
- The IP Addresses need to match the public IP addresses of the server where the Defender Security Server is installed on
- Require OTP verification as 2nd step is checked. Otherwise, users will not be prompted for OTP when logging into their machines which is your intent.
You must also make sure that your users have a user policy assigned to them that enables OTP authentication factors like OneLogin Protect or Google Authenticator.
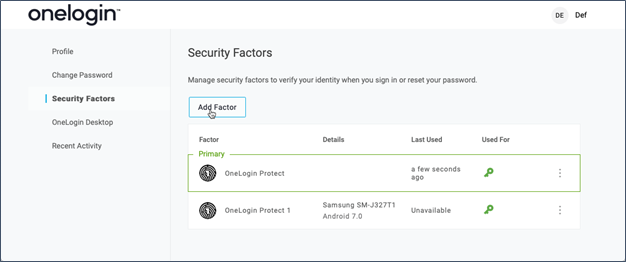
Users will then be able to register their own authentication factors from their user profile.
You can find more details on how to implement this type of integration here.
Stay tuned for more on what we are doing as we continue to build our Unified Identity Security Platform.

